Secure by Design, Secure by Default
When security is added after the fact, systems inherit weakness by design. The result is a game of cat and mouse, patching and chasing threats instead of preventing them and risk managinging anything else. Security must be built in, not bolted on.
The ACSC has published a set of Secure by Design Foundations to guide manufacturers and consumers in this effort.
Secure by Design and Secure by Default represent a fundamental shift in how we approach cybersecurity. These principles demand that security considerations be integrated into every aspect of system design, development, and deployment from day one1. The concept of secure by design has evolved significantly over the decades, with comprehensive frameworks now available to guide implementation2.
Using the following two systems we can show an example of Secure By design:
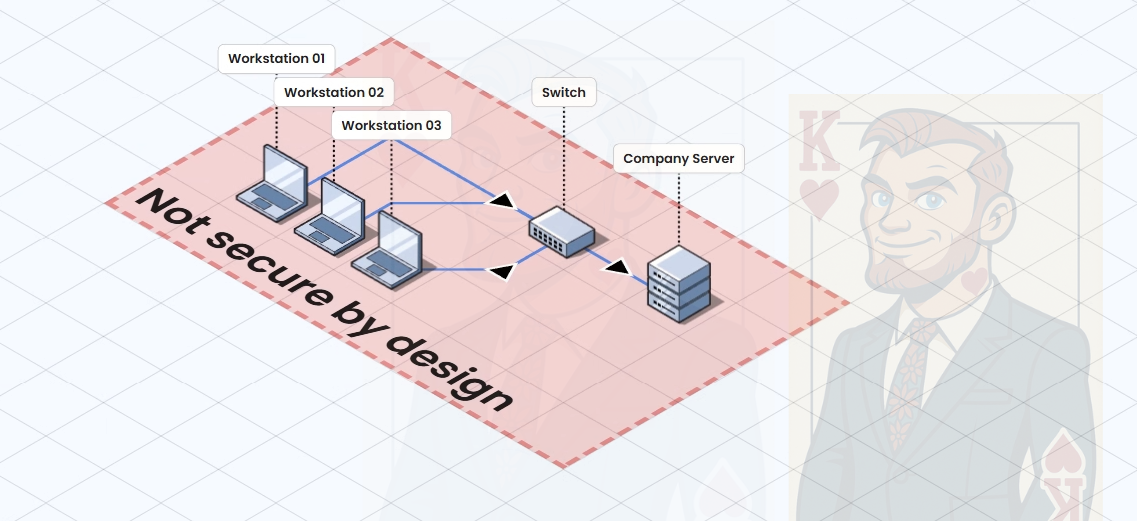
System 1: Insecure by Design ❌
During procurement the project decided to purchase laptops that did not have a TPM module. They’re running a flat network structure to save costs in network design and all users are sharing accounts as it’s easier to write the login details on a stickie note and stick them to the monitor.
Configuration Issues:
- TPM: Not present in hardware (can still do encryption at rest, just painfully with additional admin. Ask me how I know)
- OS: Windows 10 (Default Configuration)
- Authentication: Shared accounts with no password restrictions
- Network: All users use the same workstations and network
ISM Control Gaps:
- ISM-0459: No TPM implementation for hardware-based security, whilst not a complete show stopper it was found untenable to have to manage bitlocker keys and manually enter them during reboots
- ISM-2012: No screen lock policy enforcement due to default configuration
- ISM-1386: No network segmentation controls due to flat network setup
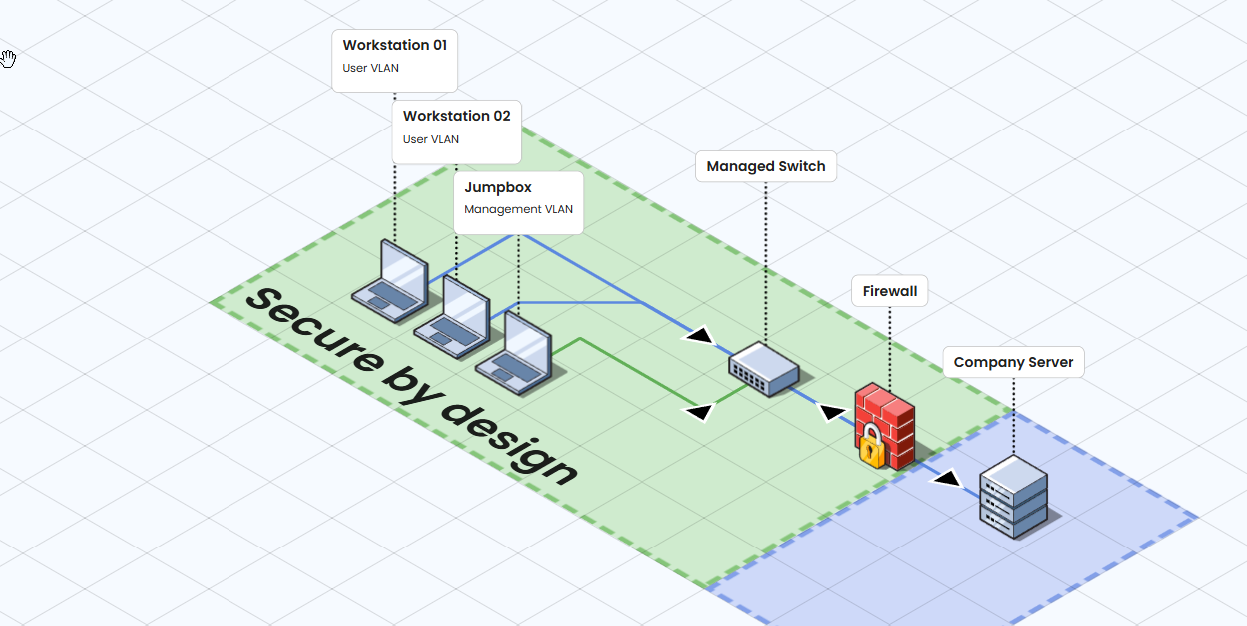
System 2: Secure by Design ✅
During procurement, the project were aware of security requirements and baked them into contracts. They procured a laptop that had a TPM and employed appropriately skilled personnel to design the system and network to meet the ISM controls applicable to their systems environment.
Configuration Implementation:
- TPM: TPM 2.0 enabled with secure boot
- OS: Windows 10 (Hardened Configuration)
- Authentication: Individual, attributable accounts are used with a naming convention
- Network: VLAN separation
ISM Control Implementation:
- ISM-0459: ✅ TPM 2.0 for hardware-based security, they now only need to access the keys when creating backups
- ISM-2012: ✅ Screen lock policy enforced after reading the ACSC hardening guide
- ISM-1386: ✅ Network segmentation controls active through the use of VLAN separation, the jump box workstation has it’s own place
Whilst achieving basic security controls, System 2 has also saved numerous man hours in POAM meetings. Well done system 2.
Conclusion
Secure by Design ensures systems achieve adequate protections through good design choices. When security is integrated early, A&A becomes a validation of good engineering, not a remediation project or another POAM item. When it’s ignored or forgotten until the end, the system inherits risk by design, and your project or system inherits costly technical debt.
In the above very simple example, we can see how a by simply choosing to procure the wrong laptop can lead to security issues down the road which cannot be corrected without time, money, and resources; it’s as simple as reviewing security requirements early and following guidance that is freely available such as the ACSC hardening guide for Windows3.
Secure by Default
Coming soon, maybe.
Footnotes
-
ACSC Definition: The Australian Cyber Security Centre (ACSC) defines Secure by Design as “a methodology that integrates security considerations into the entire system development lifecycle.” For more information, see their Secure by Design Foundations. ↩
-
Wikipedia Reference: Secure by design - Wikipedia - Comprehensive overview of secure by design principles and methodologies. ↩
-
ACSC Hardening Guide: ACSC Windows Hardening Guide - Comprehensive guidance for securing Windows workstations and implementing security controls. ↩