Alternate Data Streams
Alternate Data Streams (ADS) in NTFS
MITRE ATT&CK Mapping (T1564.004)
Overview
Alternate Data Streams (ADS) are a lesser-known feature of the NTFS file system, allowing multiple data streams to be associated with a single file. While originally designed for compatibility, attackers may exploit ADS to hide malicious payloads or artifacts.
Real-World Procedure Examples
APT32 — Used ADS to conceal payloads within benign files.
Astaroth — Stored malicious content inside ADS for payload delivery.
BitPaymer — Copied itself into a :bin ADS of a newly created file.
DEADEYE.EMBED variant — Embedded payload into an alternate data stream.
esentutl tool — Used to read/write ADS.
Expand command — Can write files into ADS.
Detection & Mitigation Strategies
Key Detection Methods:
- DS0017 – Command: Command Execution — Use
streams.exe,dir /r, or PowerShell with-Streamto find ADS. - DS0022 – File: File Metadata / Modification — Monitor file operations involving colons indicative of ADS.
- DS0009 – Process: OS API Execution / Creation — Log usage of NTFS EA APIs and execution from ADS via Sysmon.
M1022 – Restrict File and Directory Permissions — Limit NTFS EA/ADS access permissions to prevent abuse.
By integrating awareness of ADS and mapping to MITRE ATT&CK T1564.004, organizations enhance detection and defense capabilities against stealthy adversarial techniques.
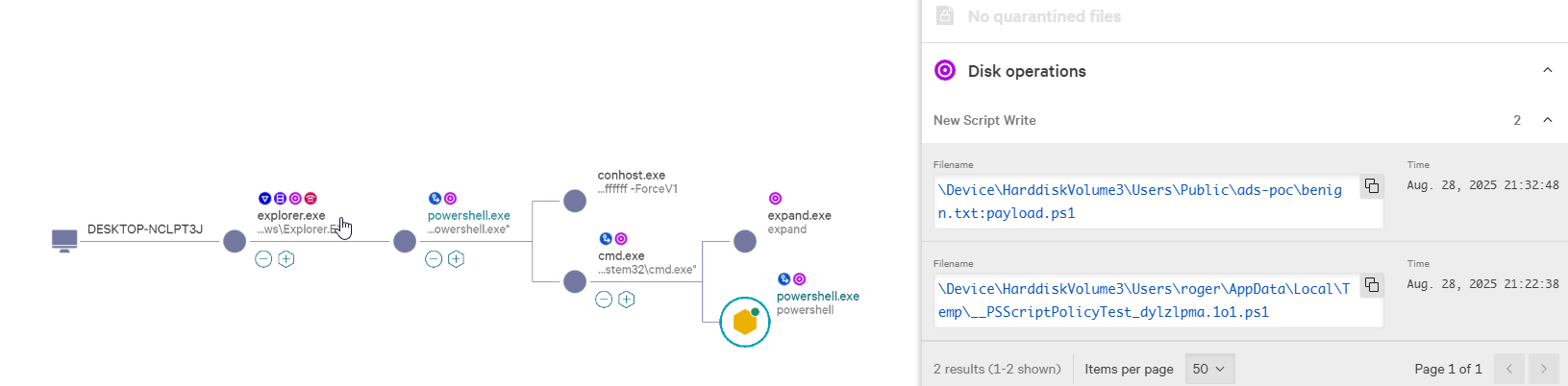
Detection Example: Crowdstrike EDR / SIEM
We can check for alternate data streams by looking at file writes with a colon within them.
NGSIEM Query
#event_simpleName=/writ/i | FileName=*:*
| table([@timestamp, FilePath, FileName])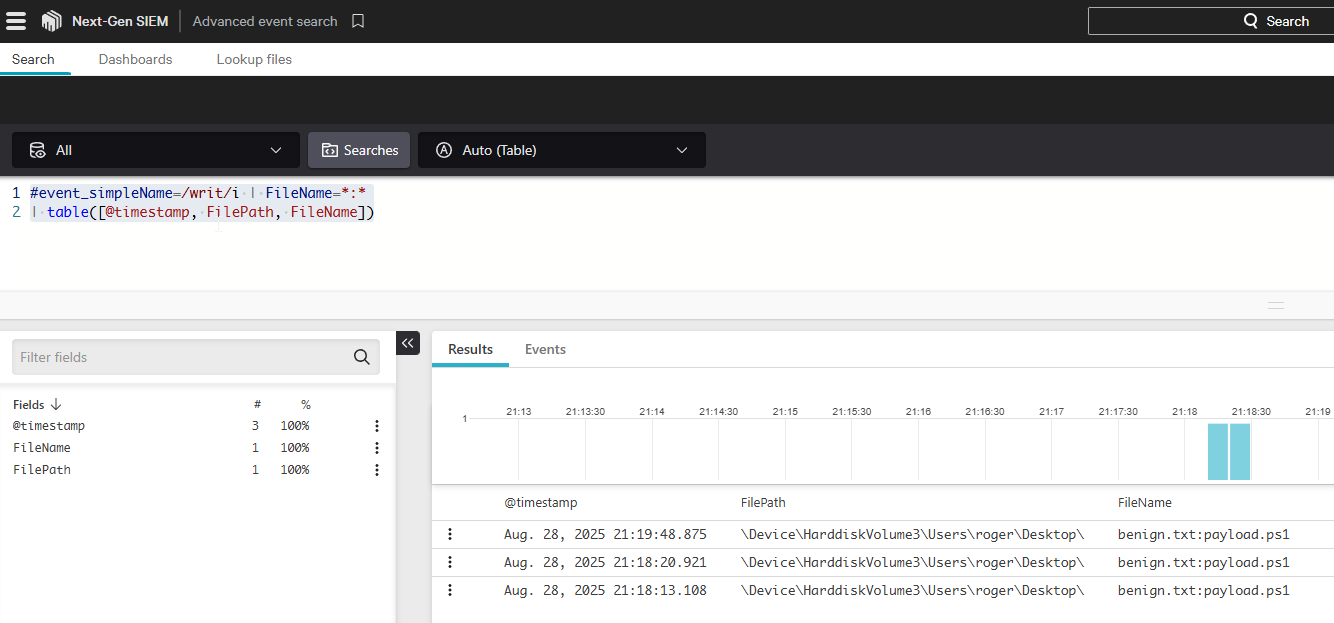
Detection Example: powershell
PS C:\Users\Public\ads-poc> Get-Item .\benign.txt -Stream *
PSPath : Microsoft.PowerShell.Core\FileSystem::C:\Users\Public\ads-poc\benign.txt::$DATA
PSParentPath : Microsoft.PowerShell.Core\FileSystem::C:\Users\Public\ads-poc
PSChildName : benign.txt::$DATA
PSDrive : C
PSProvider : Microsoft.PowerShell.Core\FileSystem
PSIsContainer : False
FileName : C:\Users\Public\ads-poc\benign.txt
Stream : :$DATA
Length : 29
PSPath : Microsoft.PowerShell.Core\FileSystem::C:\Users\Public\ads-poc\benign.txt:payload.ps1
PSParentPath : Microsoft.PowerShell.Core\FileSystem::C:\Users\Public\ads-poc
PSChildName : benign.txt:payload.ps1
PSDrive : C
PSProvider : Microsoft.PowerShell.Core\FileSystem
PSIsContainer : False
FileName : C:\Users\Public\ads-poc\benign.txt
Stream : payload.ps1
Length : 205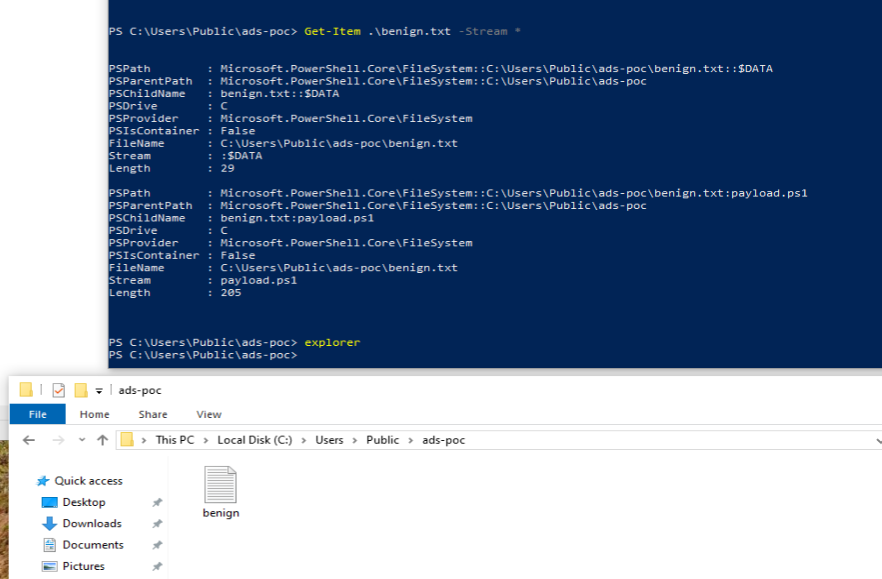
ISM Mapping
Relevant ISM Control Families
- Access Controls (AC)
- System Hardening (SH)
- Audit and Monitoring (AU)
Potential Control Alignment
-
ISM-1269 — Restricting access to system utilities
- Agencies must restrict the use of utilities and system functions that can alter files in ways that bypass normal controls.
- ADS creation/modification is an “advanced” NTFS function; restricting which accounts can write to ADS aligns with limiting such utilities.
-
ISM-1402 — Configuring file and directory permissions
- Agencies must configure file and directory permissions to follow least privilege.
- This directly maps to M1022’s principle of restricting NTFS permissions to limit ADS abuse.
-
ISM-1793 — Monitoring of security events
- Agencies must monitor for anomalous file system activity.
- While not preventing ADS directly, monitoring ADS creation/use complements NTFS permission restrictions.